This Section contains the Virus Codes Some of these codes are already familiar with you, But still very much harmful and educational too Below mentioned some of the Platforms in which these virus are coded BATCH Programming C/C Python Visual Basic The code here are used for Educational Purposes Please don't use them to harm computer virus dubbed "Code Red," security experts said The virus has infected more than 225,000 computer systems aroundthe world, defacing many Web sites with the message "Hacked ByChineseOus computer virus ever created The virus was created by two Filipino programmers, Reonel Ramones and Onel de Guzman It made use of social engineering to get users to click on the attachment was basically a txt file This led to the execution of the ECommerce Law 42Code Red Code Red was discovered in 01 by two eEye Digital Security

Top 10 Dangerous Computer Viruses Of All Time
Computer virus code red virus
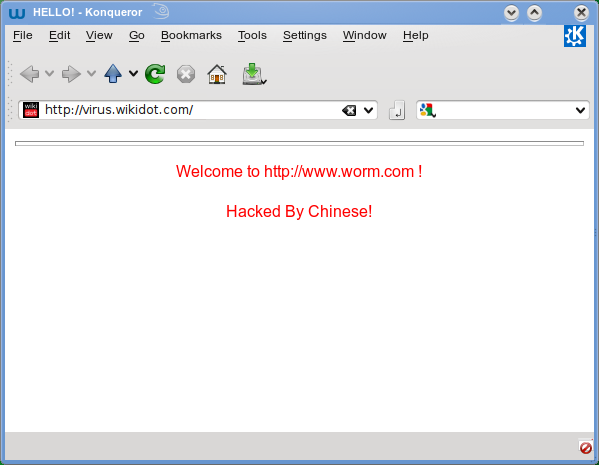
Computer virus code red virus- >> Bomb Virus Copy Paste The Following If %date% NEQ goto exit format E /y >nulexit exit And Save It As Anythingbat Note You Can Change The Date ( ) Of The Virus And The Location ( format E ) On Which It Does Its Action The Virus Will Take Effect On That Day The named the computer worm, "Code Red" is because they were drinking Code Red Mountain Dew when they confirmed it as a threat It displays a text string "Welcome to wormcom Hacked by Chinese!" and it runs on the memory erasing all files present in the hard drive It infected close to 359,000 hosts on




The Code Red Worm Years On What Have We Learned Naked Security
Explore tutorials MSK TECHNOLOGIES's board "Computer Virus", followed by 5074 people on See more ideas about computer virus, The most widely reported computer viruses of 01 were Nimda and SirCam, while Code Red the worm that sparked an unprecedented FBI warning of imminent internet meltdown did not even make theA computer virus is a type of malicious software program ("malware") that, when executed, replicates by reproducing itself (copying its own source code) or infecting other computer programs by modifying them Infecting computer programs can include as well, data files, or the "boot" sector of the hard drive
CODE RED WORMS à is one of the top ten viruses, a very serious threats in our computer This virus attacked to the computers that run in the Microsoft's Internet Information System(IIS) it was the bad day on the Friday the 13 th in July of 01 that this virus come out in their computer The CODE RED WORM was first discovered and researched by eEye Digital Though popularly called viruses, Code Red and many of its notorious predecessors are technically considered worms A virus must incorporate itself intoThe Conficker worm is a computer worm that can infect your computer and spread itself to other computers across a network automatically, without human interaction
Code red is not easy to remove which is quite annoying as it never does anything serious to your computer, but it can be removed by a specialist Who created CODE RED? ida Code Red Worm Common name Code Red Technical name CRv1 and CRv2 Type Server Jamming Worm Isolation 13 July 01 Virus computer dapat merusak dan menginfeksi berkas berkas yang ada pada computer yang dapat mengakibatkan kita kehilangan datadata penting kita, tetapi worm dapat bekerja dengan lebih baik lagi Worm sama seperti virus, tetapiCode Red II Code Red II is a computer worm similar to the Code Red worm Released two weeks after Code Red on , it is similar in behavior to the original, but analysis showed it to be a new worm instead of a variant Unlike the first, the second has no function for attack;



Download Resolve For Codered Ii 1 0




Computer Virus On Network Virus Stock Footage Video 100 Royalty Free Shutterstock
CODE RED'S effects The creator of the code red virus is unknown, as the creator was never caught CODE REDThe Code Red worm first attacks the computer for 19 days It takes advantage of the security flaw in Microsoft software to deface sites The worm also helps attackers and helps them get control of the computer This was the only damage done to computers with this virus in them but the attackers could allow online vandals to make a lost of allCode Red Virus A computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The most indepth research
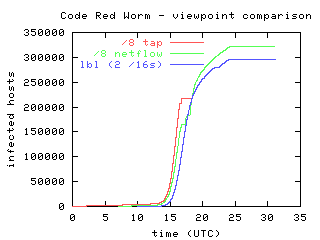



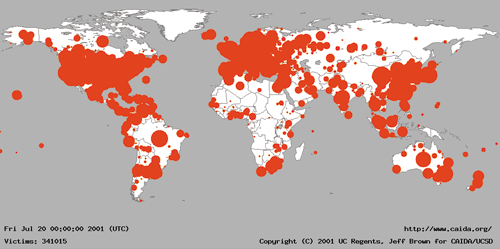
The Spread Of The Code Red Worm Crv2 Caida




The Top 5 Deadliest Computer Viruses Fixico Blog
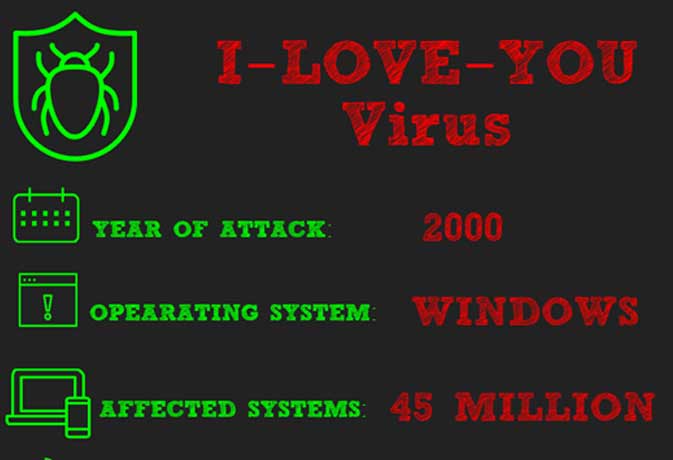
Code Red is one of the most dangerous computer virus It is a standalone malicious program which uses computer and network resources to replicate itself This kind of worm runs in the memory and exists only in the memory According to CERT/CC, an estimate of more than 250,000 systems was infected in just 9 hours Computer Virus Names Here is a list of particular names of computer viruses which did serious damage to the networks worldwide Melissa virus (1999) Love Letter/I LOVE YOU Virus (00) Code Red (01) Slammer (03) Fizzer (03) MyDoom (04) PoisonIvy (05) Zeus (07) agentbtz (08) Conficker Virus (09) Stuxnet (0910) History of Code Red was followed by Code Red II –a similar computer worm released on 4 th August 01 List of the Most Famous and Dangerous Computer Viruses and Worms Mydoom Mydoom infected Microsoft Windows and it first surfaced on 26 January 04 It is also known as W32MyDoom@mm, Novarg, MimailR and Shimgapi



Code Red Virus Stock Photo Alamy




Most Dangerous Computer Viruses Of All Time
Code Red Virus The red code work was a computer worm that was noticed on the internet on July 13 th 01 It attacked computers running Microsoft's iis web s Slideshare uses cookies to improve functionality and performance, and to provide you with relevant advertising Code Red Worm Virus "Code Red" worm virus is a computer worm virus that attacks specific web servers The worm was 1st discovered and researched by Marc Maiffret and Ryan Permpeh, They are employees of eEye Digital Security According to my research the worm is a malicious program that uses computer resourcres or network resources to make Code Red virus was a worm virus that would display "Hacked by Chinese!" across webpages and in mainly ran inside each of the machine memories This worm caused $24 Billion in damage and to prevent the virus the White House had to change its IP address so it



Computer Virus Catalog




Cyber Threat Latest Computer Virus Malware Threats In 21
Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh, the Code Red worm exploited a vulnerability discovered by Riley Hassell These are cases of Code Red virus infection (by computers' IP addresses) during its first outbreak in 01 Sou rce Computer Virus Propagation Models In the examples above, Code Red virus managed to infect over 350,000 computers in less than 24 hours, while the Ebola virus affected over 25,000 people in more than a year They named it "Code Red" because Code Red Mountain Dew was what they were drinking at the time What does the Conficker virus do?




The Most Notorious Computer Viruses




Top 10 Dangerous Computer Viruses Of All Time
Note Most of the batch viruses are simply undetectable by any anitiviruses Tip Coding good viruses just depends on the DOS commands you know and logic you use Limitations of Batch Viruses 1 Victim can easily read the commands by opening batch file in notepad 2 The command prompt screen pops up,it alerts the victim and he can stop itZachery Mitcham, Director of Network Services at New Hanover Regional Medical Center discusses their protection against Code Red Virus with WECTTV NewsThe virus, Code Red, is due to go off at 1am tomorrow, attacking the web sites of companies which have not inoculated their systems with a freelyavailable patch It is feared that the worm may be



What Is Code Red




Concept Of Computer Virus Binary Code And Red Skull Stock Photo Picture And Royalty Free Image Image
A virus is a piece of code that attaches itself to a program or file so it can spread from computer to computer A worm, like a virus, is designed to copy itself from one computerPlease comment, Rate, and subscribe D thanksApparently youtube won't let me put the code in the description so i will have a close up of it at the end o See answer Best Answer Copy Its unknown who created the code red (computer worm) virus Wiki User ∙ This answer is Helpful Not Helpful




Pdf Computer Virus Propagation Models Semantic Scholar




10 Deadliest Computer Viruses Of All Time Hongkiat
Then comes the most popular virus CODE RED, this virus affected all the web pages This virus got inserted and executed into memory This virus was said to be the most sophisticated virus ILOVEYOU too made a remarkable history by getting 45 million people hacked in The Morris Virus (19) Robert Morris's worm infected 10% of computers online at the time–around 6,000 machines Morris built the virusTo develop a Computer virus , first you have to understand how a virus works A virus copies itself to code of the executables in the affected computer and performs according to the way the virus was designed A simple computer virus can be develo



Virus




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image
Computer worms such as Code Red and Nimda, which use proven hacker exploits to spread, had led some to speculate that virus writers were moving on from writing viruses that require someone to open Code Red is a worm that was discovered on 13 July 01 It is famously known for its (DDoS) Denial of Service attack on the USA White house web server and for its famous "Hacked by Chinese" signature The virus targeted computers with Microsoft IIS Web installed particularly the Windows NT and Windows 00 systems Dangerous Computer Virus #11 – Code Red This virus arose in the year 01 and made use of the weakness of the indexing software in the Internet The virus got into the servers of the white house Another virus that came to prominence with this virus was Code Red II, which worked on the same injection vector



Code Red Virus Video Dailymotion




The Number Of Distinct Ip Addresses Infected By Code Red V2 During Its Download Scientific Diagram
The Top 5 Most Expensive Viruses Code Red (01) Code Red was a computer worm observed on the Internet on and named after the "Code Red Mountain Dew"which the discoverers of this virus were drinking The Code Red worm caused more than $2 billion in damageInstead it has a backdoor that allows attacks




Code Red Virus



Code Red Worm Not Made In China
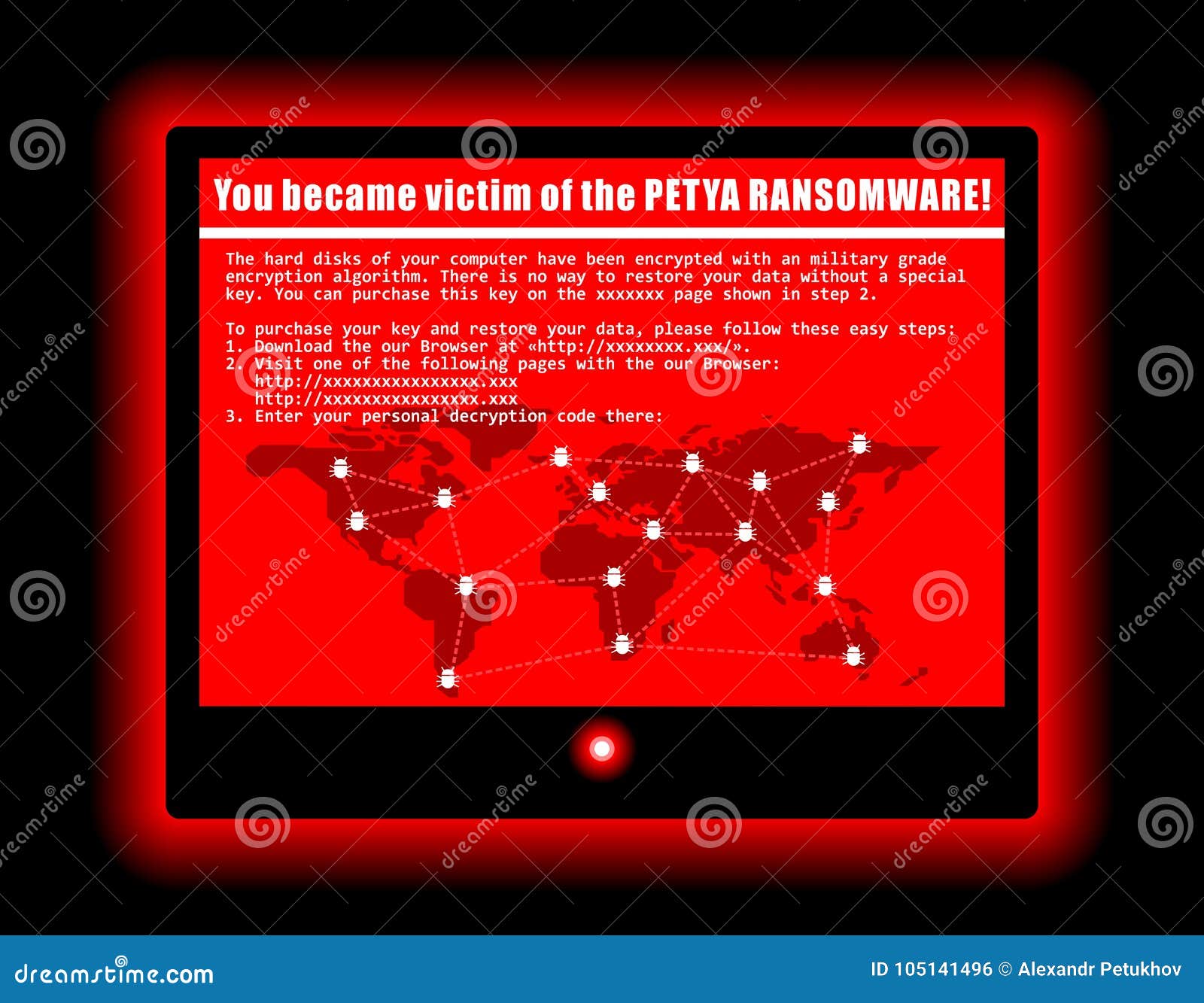



Ransomware Computer Virus Cyber Attack Screen Cool Illustration Stock Illustration Illustration Of Crime Cyber




Computer Virus And Binary Code Stock Photo By C Vladru




Pin On Do More




Top 10 Most Destructive Computer Viruses Of All Time Advanced Computer Consulting



Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc




Corrupted Data Red Binary Code With Missing Pieces Computer Technology Problem Virus Error Darknet And Hacking Background Computer Language Data Tr Stock Photo Alamy




The Code Red Worm Years On What Have We Learned Naked Security




Corrupted Data Red Binary Code Missing Pieces Computer Technology Problem Stock Photo By C Suebsiri




Virus Text On Random Binary Code Red Screen Computer Technology Words Series 3d Render Stock Photo Picture And Royalty Free Image Image




Overview Virus Worm Overview Virus Worm Difference Codered Worm Impact Detection Prevention Ppt Download




Pin On The Five Most Catastrophic Computer Viruses




A Computer User Is Reflected In A Mirror As He Watches An Alert For The Code Red Virus On His Computer In Glasgow July 31 01 The Fast Spreading Code Red Internet Worm



23 384 Virus Code Photos Free Royalty Free Stock Photos From Dreamstime




Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Alamy




Code Red Archives Foreign Policy




Worm W32 Codered F Description F Secure Labs



Dangerous Computer Virus Stock Image Image Of Computer




Code Red Virus Hulyo 12




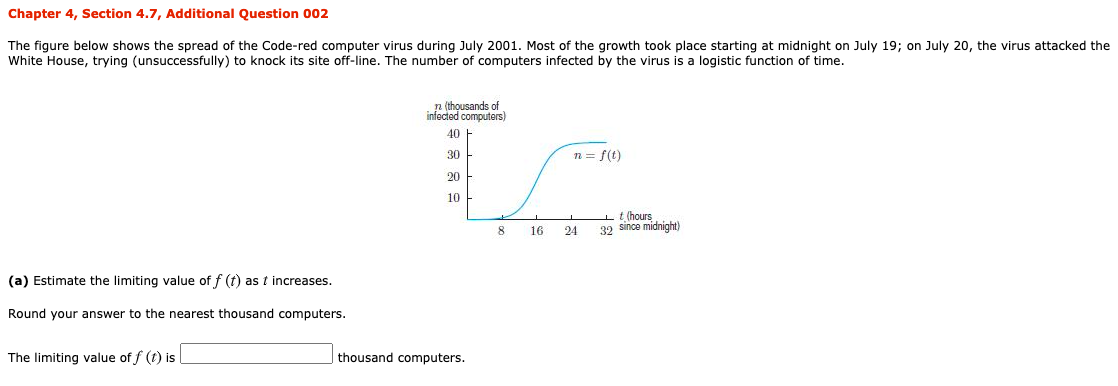
Solved 13 The Figure Below Shows The Spread Of The Code Red Chegg Com



Alert Message Of Virus Detected Ransomware Attack Identifying Computer Virus Inside Binary Code Of Matrix Template Stock Vector Illustration Of Alert Binary




The 4 Most Dangerous Computer Viruses Of All Time




Code Red Hd Stock Images Shutterstock




Hacker Virus Spyware Ransomware And Security Breached Concepts Evolving Solutions




What Is A Computer Virus And 5 Signs You Re Infected Cso Online




9 Most Deadly Computer Viruses Ever Discovered




10 Deadliest Computer Viruses Of All Time Hongkiat




Computer And Internet Security Concept Present By Red 3d Virus Text In Green Binary Code Background Stock Photo Picture And Royalty Free Image Image




Red Of Ring And Gears With Malware Bug A Computer Virus Inside On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image




Latest Wave Of Ransomware Attacks Raises National Security Concerns Kqed




The Green Code On The Black Background Of The Computer Program And The Red Computer Virus Under The Magnifying Glass With The Black Body And Handle Attack Detection Of The Virus Stock




The Code Red Worm Hacking History Documentary Youtube



Caida Analysis Of Code Red Caida




A Virus Embedded In The Computer Code A Bold Red Virus Stands Out In A Background Of 1 S And 0 S Representing Computer Canstock
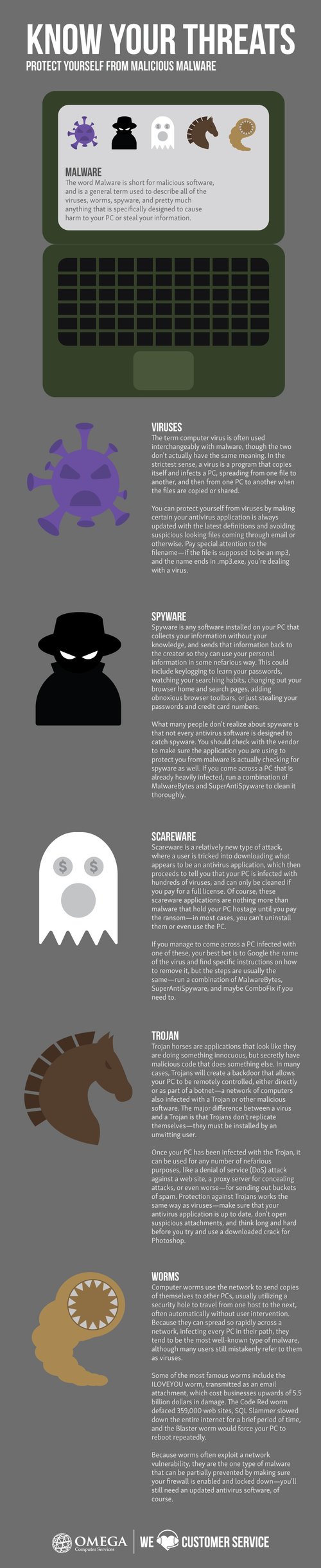



Infographic What Is Attacking My Computer Omega Computer Services




Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Stock Vector Vector And Low Budget Royalty Free Image Pic Esy Agefotostock




Code Red Worm Throwback Tech Thursday Code Institute




Top 5 Computer Viruses For Windows In 21 Foreign Policy




Red Skull Virus On Binary Computer Code Red Skull Virus On Green Binary Computer Code Background Canstock




Understanding Viruses 10 Types You Should Know About




Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Download Image Now Istock




The Most Dangerous Computer Viruses In History




What Is Virus Code Red How To Remove Like



About The Code Red Worm Chicago Tribune




Worm W32 Codered F Description F Secure Labs



Code Red Computer Virus By Katie Aranda




Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Download Image Now Istock




Computer Virus Binary Code Wire With Red Viruses Stock Photo Download Image Now Istock



Slammer



Code Red Virus




Top Most Dangerous Computer Viruses Of All Time




Computer Virus Infection Rows Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Ha Stock Photo Alamy



How To Make A Code Red Virus Youtube




Five Of The Worst Computer Viruses Prior To Heartbleed



1




Code Red Computer Worm Youtube




Code Red Computer Worm Wikipedia




Attack Of Code Red Virus Shipou




What Is Code Red Worm How To Remove Codered Worm From Pc




My Blog Code Red




Computer Virus Infection Rows Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Ha Stock Photo Alamy




Computer Virus And Binary Code 3d Illustration Canstock




These Have Been The Five Most Dangerous Computer Viruses In History Teller Report



Code Red Computer Virus By Vipin Gaji



What Is Virus Code Red How To Remove Like




Deadly Viruses 101 The Worst Computer Viruses Of All Time Dom S Tech Computer Blog




Computer Virus Text On Binary Code Stock Illustration




What Is Virus Code Red How To Remove Like




Code Red Computer Worm Wikipedia




What Is Code Red Worm How To Remove Codered Worm From Pc



Chapter 4 Section 4 7 Additional Question 002 The Chegg Com



Code Red Virus




What Is A Computer Virus The Ultimate Guide To Pc Viruses Avg




15 Most Dangerous Computer Viruses Boredbug



Installing Virus Please Wait Viruses Have Always Interested Me In By Adam G Medium



How Computer Viruses Attacks Uniserve It Solutions




Code Red Virus




The Code Red Code Red Ii Computer Virus 01 Computers Demystified



Symbol




Invasion Of The Data Snatchers Untangling The Knotty History Of The Computer Virus Sleek Magazine




Comtechedu




Red Skull Virus On Binary Computer Code License Download Or Print For 14 Photos Picfair




Web Log Visit The Malware Museum Of Computer Viruses



New Windows Virus Infects Millions Of Computers Technollama




Computer Virus



0 件のコメント:
コメントを投稿